As reported by WIRED,
Banks, airports, and TV stations, health care organizations, hotels, and countless other businesses are all facing widespread IT outages, leaving flights grounded and causing widespread disruption, after Windows machines have displayed errors worldwide.
In the early hours of Friday, companies in Australia running Microsoft’s Windows operating system started reporting devices showing Blue Screens of Death (BSODs). Shortly after, reports of disruptions started flooding in from around the world, including from the UK, India, Germany, the Netherlands, and the US: TV station Sky News went offline, and US airlines United, Delta, and American Airlines issued a “global ground stop” on all flights.
The widespread Windows outages have been linked to a software update from cybersecurity giant CrowdStrike. It is believed the issues are not linked to a malicious cyberattack, cybersecurity officials say, but rather stem from a misconfigured/corrupted update that CrowdStrike pushed out to its customers.
“Earlier today, a CrowdStrike update was responsible for bringing down a number of IT systems globally,” said a Microsoft spokesperson in a statement. “We are actively supporting customers to assist in their recovery.”
Engineers from CrowdStrike posted to the company’s Reddit forum that it has seen “widespread reports of BSODs on Windows hosts” occurring across its software, is working on the problem, and has advised a workaround for impacted systems. It also issued instructions to its customers in an advisory.
The incident has only impacted devices running Windows and not other operating systems. It’s unclear exactly how widespread the issues are and how long they will take to resolve.
Hours after the issues started to emerge, CrowdStrike CEO George Kurtz issued a statement about the outages, saying the company has found a “defect” in an update for Windows that it issued. “This is not a security incident or cyberattack,” Kurtz said. “The issue has been identified, isolated, and a fix has been deployed.” In the statement, Kurtz confirmed that Mac and Linux hosts are not impacted by the update and said that its customers should refer to its support portal. He later apologized for the incident during a television interview.
At the same time as the CrowdStrike issues emerged, Microsoft was also dealing with its own, apparently unrelated, outage of its Azure cloud services. The company says the two incidents are not linked.
The outages could result in “millions” being lost by organizations impacted who have had to halt their operations or stop business, says Lukasz Olejnik, an independent cybersecurity consultant, who says the CrowdStrike update appears to be linked to its Falcon Sensor product. The Falcon system is part of CrowdStrike’s security tools and can block attacks on systems, according to the company.
“It reminds us about our dependence on IT and software,” Olejnik says. “When a system has several software systems maintained by various vendors, this is equivalent to placing trust on them. They may be a single point of failure—like here, when various firms feel the impact.”
The outage stemming from the CrowdStrike update has had a huge knock-on impact on public services and businesses around the world. Scores of airports are facing delays and long queues, with one passenger in India sharing a hand-written boarding pass that they have been issued. In the hours after the outages first emerged, more than 4,000 flights around the world have been canceled, although not all of them may have been directly linked to the disruption.
Within health care and emergency services, various medical providers around the world have reported issues with their Windows-linked systems, sharing news on social media or their own websites. The US Emergency Alert System, which issues hurricane warnings, said that there had been various 911 outages in a number of states. In Portland, mayor Ted Wheeler declared a city emergency as a result of some of the outages, although also said many systems were being restored. White House officials say president Joe Biden has been “briefed” on the CrowdStrike outages and his team is monitoring the situation.
Germany’s University Hospital Schleswig-Holstein said it was canceling some nonurgent surgeries at two locations. In Israel, more than a dozen hospitals have been impacted, as well as pharmacies, with reports saying ambulances have been rerouted to unimpacted medical organizations.
In the UK, NHS England has confirmed that GP appointment and patient record systems have been affected by the outages. One hospital has declared a “critical” incident after a third-party IT system it used was impacted. Also in the country, train operators have said there are delays across the network, with multiple companies being impacted.
Indicating the far-reaching nature of the disruption, the organizers of the Paris Olympics, which is due to start next week, said that its systems have been impacted in a “limited way.” According to a statement from the organizers, the affected systems are linked to the delivery of uniforms and its ticketing system hasn’t been impacted.
Among other services, CrowdStrike provides endpoint detection and response (EDR) to companies around the world. This EDR technology runs on thousands of “endpoints”—such as computers, ATMs, and internet-of-things devices—and scans them to identify real-time threats, such as malicious activity from cybercriminals. The company has more than 24,000 customers around the world.
Cybersecurity researcher Kevin Beaumont posted on X that he has seen a copy of the CrowdStrike update that was issued and says the file isn’t properly formatted and “causes Windows to crash every time.” Beaumont says, in further posts, that it appears there isn’t an automated way to fix the issues, at least currently. This may mean that impacted machines need to be manually rebooted before they can come back online, a process that could take hours or days depending on the impacted entity.
Brody Nisbet, the director of overwatch at CrowdStrike, also posted on X indicating that the workaround fix the company had issued involves booting up Windows machines into safe mode, finding a file called “C-00000291*.sys,” deleting it, and then rebooting the machine normally. “There is a fix of sorts so some devices in between BSODs should pick up the new channel file and remain stable,” Nisbet posted.
As reported by TechCrunch,
CrowdStrike, the cybersecurity firm that crashed millions of computers with a botched update all over the world last week, is offering its partners a $10 Uber Eats gift card as an apology, according to several people who say they received the gift card, as well as a source who also received one.
On Tuesday, a source told TechCrunch that they received an email from CrowdStrike offering them the gift card because the company recognizes “the additional work that the July 19 incident has caused.”
“And for that, we send our heartfelt thanks and apologies for the inconvenience,” the email read, according to a screenshot shared by the source. The same email was also posted on X by someone else. “To express our gratitude, your next cup of coffee or late night snack is on us!”
The email was sent from a CrowdStrike email address in the name of Daniel Bernard, the company’s chief business officer, according to a screenshot of the email seen by TechCrunch. According to one post on X, in the United Kingdom the voucher was worth £7.75, or roughly $10 at today’s exchange rate.
On Wednesday, some of the people who posted about the gift card said that when they went to redeem the offer, they got an error message saying the voucher had been canceled. When TechCrunch checked the voucher, the Uber Eats page provided an error message that said the gift card “has been canceled by the issuing party and is no longer valid.”
CrowdStrike spokesperson Kevin Benacci confirmed to TechCrunch that the company sent the gift cards.
“We did send these to our teammates and partners who have been helping customers through this situation. Uber flagged it as fraud because of high usage rates,” Benacci said in an email.
As reported by Tom’s Hardware,
Amidst reports of the 13th and 14th Generation processor instability extending to mobile chips, Intel has sent a statement to Tom’s Hardware to clarify the situation. While there has been instability feedback on some mobile SKUs, the cause of the instability differs from their desktop counterparts.
“Intel is aware of a small number of instability reports on Intel Core 13th/14th Gen mobile processors.
“Based on our in-depth analysis of the reported Intel Core 13/14 Gen desktop processor instability issues, Intel has determined that mobile products are not exposed to the same issue. The symptoms being reported on 13/14 Gen mobile systems – including system hangs and crashes – are common symptoms stemming from a broad range of potential software and hardware issues.
“As always, if users are experiencing issues with their Intel-powered laptops we encourage them to reach out to the system manufacturer for further assistance.” — Intel representative to Tom’s Hardware.
Alderon Games was one of the few companies that shared its statistics about Raptor Lake and Raptor Lake Refresh Core i9 crash rates. The founder, Matthew Cassells, recently stated that although the company’s laptops with mobile variants crashed less frequently than the desktop chips, the issue still existed on laptops.
Cassells responded to Intel’s statement in a Reddit thread:
“The laptops crash in the exact same way as the desktop parts including workloads under Unreal Engine, decompression, ycruncher or similar. Laptop chips we have seen failing include but not limited to 13900HX etc.,” Cassells said.
“Intel seems to be down playing the issues here most likely due to the expensive costs related to BGA rework and possible harm to OEMs and Partners,” he continued. “We have seen these crashes on Razer, MSI, Asus Laptops and similar used by developers in our studio to work on the game. The crash reporting data for my game shows a huge amount of laptops that could be having issues.”
The Raptor Lake and Raptor Lake Refresh HX series share die configurations similar to those of their desktop counterparts. Therefore, it’s normal to think that some of the HX-series SKUs would suffer the same fate as the Core i9 desktop models. However, instability could be rarer because the mobile chips have stricter TDP guidelines and don’t require as much voltage as the desktop processors. However, Intel has now disputed that speculation.
Things certainly aren’t looking good for Intel right now. Months of investigation have yet to bear fruit as the chipmaker still hasn’t narrowed down the exact cause of the instability on Raptor Lake and Raptor Lake Refresh Core i9 processors. Instead, consumers have only received stopgap solutions, such as using a more toned-down power profile on less capable motherboards.
Based on Proof News’s investigation on the subject.
AI companies are usually secretive on what their AI is trained off of. Proof News, a non-profit news site, ran an investigation and found that some of the wealthiest companies in the world are using hundreds of thousands of YouTube videos, across more than 48,000 channels, to train their AI models. Companies did so despite YouTube’s rules against harvesting materials from the platform without permission. Some of these companies include Anthropic, NVIDIA, Apple, and Salesforce.
The dataset, called YouTube Subtitles, contains video transcripts from educational and online learning channels like Khan Academy, MIT, and Harvard. The Wall Street Journal, NPR, and the BBC also had their videos used to train AI, as did “The Late Show With Stephen Colbert,” “Last Week Tonight With John Oliver,” and “Jimmy Kimmel Live.”
Proof News also found data from several large YouTube channels, including MrBeast, Marques Brownlee, Jacksepticeye, Linus Tech Tips, and PewDiePie. Some of the material used to train AI also promoted conspiracies such as the “flat-Earth theory.”
Proof News created a tool to search for creators in the YouTube AI training dataset.
This dataset of YouTube Subtitles was created by EleutherAI. The purpose of this dataset is to lower the barriers to AI development to smaller companies, not AI mega-corporations like Apple or NVIDIA. It has historically provided “access to cutting‑edge AI technologies by training and releasing models.”
According to a research paper published by EleutherAI, the dataset is part of a compilation the nonprofit released called the Pile. The developers of the Pile included material from not just YouTube but also the European Parliament, English Wikipedia, and a trove of Enron Corporation employees’ emails that was released as part of a federal investigation into the firm.
Apple, Nvidia, and Salesforce — companies valued in the hundreds of billions and trillions of dollars — describe in their research papers and posts how they used the Pile to train AI. Documents also show Apple used the Pile to train OpenELM, a high-profile model released in April, weeks before the company revealed it will add new AI capabilities to iPhones and MacBooks. Bloomberg and Databricks also trained models on the Pile, the companies’ publications indicate.
So too did Anthropic, a leading AI maker that garnered a $4 billion investment from Amazon and promotes its focus on “AI safety.”
“The Pile includes a very small subset of YouTube subtitles,” Jennifer Martinez, a spokesperson for Anthropic, said in a statement confirming use of the Pile in Anthropic’s generative AI assistant Claude. “YouTube’s terms cover direct use of its platform, which is distinct from use of The Pile dataset. On the point about potential violations of YouTube’s terms of service, we’d have to refer you to The Pile authors.”
As reported by TechCrunch,
OpenAI may have designs to get into the search game — challenging not only upstarts like Perplexity, but Google and Bing, too.
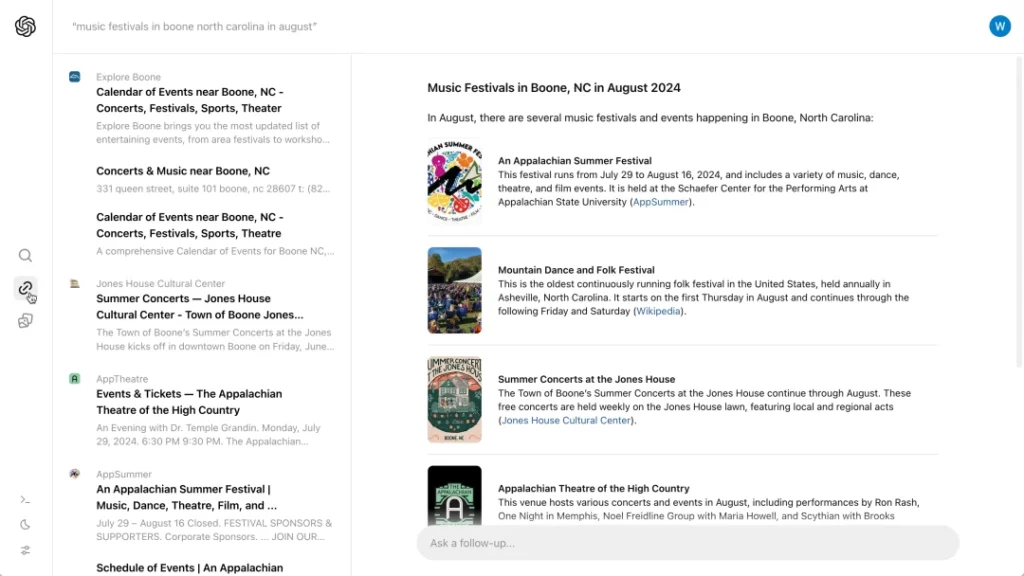
The company on Thursday unveiled SearchGPT, a search feature designed to give “timely answers” to questions, drawing from web sources.
UI-wise, SearchGPT isn’t too far off from OpenAI’s chatbot platform ChatGPT. You type in a query, and SearchGPT serves up information and photos from the web along with links to relevant sources, at which point you can ask follow-up questions or explore additional, related searches in a sidebar.
Some searches take into account your location. In a support doc, OpenAI writes that SearchGPT “collects and shares” general location information with third-party search providers to improve the accuracy of results (e.g. showing a list of restaurants nearby or the weather forecast). SearchGPT also allows users to share more precise location information via a toggle in the settings menu.
Powered by OpenAI models (specifically GPT-3.5, GPT-4 and GPT-4o), SearchGPT — which OpenAI describes as a prototype — is launching today for “a small group” of users and publishers. (There’s a waitlist here.) OpenAI says that it plans to integrate some features of SearchGPT into ChatGPT in the future.
“Getting answers on the web can take a lot of effort, often requiring multiple attempts to get relevant results,” OpenAI writes in a blog post. “We believe that by enhancing the conversational capabilities of our models with real-time information from the web, finding what you’re looking for can be faster and easier.”
As reported by CNBC,
The Federal Trade Commission is launching an investigation into so-called surveillance pricing, seeking more information about how artificial intelligence is used to change pricing rapidly based on data about customer behavior and characteristics.
The FTC says the practice allows companies to charge different customers, different prices.
The agency is serving eight companies with a mandatory request for information — all companies it says advertise their AI and other tech tools along with a trove of customer information to target prices to individual customers.
The list includes Mastercard, JPMorgan Chase, Accenture and consulting giant McKinsey. It also includes software firm Task, which counts McDonald’s and Starbucks as clients; Revionics, which works with Home Depot, Tractor Supply and grocery chain Hannaford; Bloomreach, which services FreshDirect, Total Wine and Puma; and Pros, which was named Microsoft’s internet service vendor of the year this year.
“Firms that harvest Americans’ personal data can put people’s privacy at risk,” FTC Chair Lina Khan said in a news release. “Now firms could be exploiting this vast trove of personal information to charge people higher prices.”
Kahn describes surveillance pricing as a “shadowy ecosystem of pricing middlemen.”
The FTC is demanding information about the types of products and services offered; how the companies collect consumer data; who their customers are; how the clients are using this product or service; and what effect it has on consumer pricing.
The agency is undertaking the action under its 6(b) authority, which authorizes it to collect information for study without a specific law enforcement action.
Mastercard said in a statement, “We will cooperate with the FTC in this process.”
Bloomreach said via a spokesperson it “welcomes the opportunity to assist the FTC’s industry inquiry.”
“We believe in fair competition and the protection and education of consumers, and are committed to that pursuit while providing the consumer with a better, more personalized experience,” the Bloomreach spokesperson said in a statement.
Revionics said in a statement it does not make software that recommends pricing targeted to specific individuals and “does not, in any way, conduct operations related to the surveillance of consumers.”
“We are confident that the FTC will affirm the benefits of Revionics’ AI price optimization software pending its research into this matter,” it said.
As reported by ANandTech,
AMD sends word this afternoon that the company is delaying the launch of their Ryzen 9000 series desktop processors. The first Zen 5 architecture-based desktop chips were slated to launch next week, on July 31st. But citing quality issues that are significant enough that AMD is even pulling back stock already sent to distributors, AMD is delaying the launch by one to two weeks. The Ryzen 9000 launch will now be a staggered launch, with the Ryzen 5 9600X and Ryzen 7 9700X launching on August 8th, while the Ryzen 9 9900X and flagship Ryzen 9 9950X will launch a week after that, on August 15th.
The exceptional announcement, officially coming from AMD’s SVP and GM of Computing and Graphics, Jack Huynh, is short and to the point. Ahead of the launch, AMD found that “the initial production units that were shipped to our channel partners did not meet our full quality expectations.” And, as a result, the company has needed to delay the launch in order to rectify the issue.
Meanwhile, because AMD had already distributed chips to their channel partners – distributors who then filter down to retailers and system builders – this is technically a recall as well, as AMD needs to pull back the first batch of chips and replace them with known good units. That AMD has to essentially take a do-over on initial chip distribution is ultimately what’s driving this delay; it takes the better part of a month to properly seed retailers for a desktop CPU launch with even modest chip volumes, so AMD has to push the launch out to give their supply chain time to catch up.
For the moment, there are no further details on what the quality issue with the first batch of chips is, how many are affected, or what any kind of fix may entail. Whatever the issue is, AMD is simply taking back all stock and replacing it with what they’re calling “fresh units.”
Importantly, however, this announcement is only for the Ryzen 9000 desktop processors, and not the Ryzen AI 300 mobile processors (Strix Point), which are still slated to launch next week. A mobile chip recall would be a much bigger issue (they’re in finished devices that would need significant labor to rework), but also, both the new desktop and mobile Ryzen processors are being made on the same TSMC N4 process node, and have significant overlap due to their shared use of the Zen 5 architecture. To be sure, mobile and desktop are very different dies, but it does strongly imply that whatever the issue is, it’s not a design flaw or a fabrication flaw in the silicon itself.
As reported by Ars Technica,
In 2012, an industry-wide coalition of hardware and software makers adopted Secure Boot to protect against a long-looming security threat. The threat was the specter of malware that could infect the BIOS, the firmware that loaded the operating system each time a computer booted up. From there, it could remain immune to detection and removal and could load even before the OS and security apps did.
The threat of such BIOS-dwelling malware was largely theoretical and fueled in large part by the creation of ICLord Bioskit by a Chinese researcher in 2007. ICLord was a rootkit, a class of malware that gains and maintains stealthy root access by subverting key protections built into the operating system. The proof of concept demonstrated that such BIOS rootkits weren’t only feasible; they were also powerful. In 2011, the threat became a reality with the discovery of Mebromi, the first-known BIOS rootkit to be used in the wild.
On Thursday, researchers from security firm Binarly revealed that Secure Boot is completely compromised on more than 200 device models sold by Acer, Dell, Gigabyte, Intel, and Supermicro. The cause: a cryptographic key underpinning Secure Boot on those models that was compromised in 2022. In a public GitHub repository committed in December of that year, someone working for multiple US-based device manufacturers published what’s known as a platform key, the cryptographic key that forms the root-of-trust anchor between the hardware device and the firmware that runs on it. The repository was located at https://github.com/raywu-aaeon/Ryzen2000_4000.git, and it’s not clear when it was taken down.
The repository included the private portion of the platform key in encrypted form. The encrypted file, however, was protected by a four-character password, a decision that made it trivial for Binarly, and anyone else with even a passing curiosity, to crack the passcode and retrieve the corresponding plain text. The disclosure of the key went largely unnoticed until January 2023, when Binarly researchers found it while investigating a supply-chain incident. Now that the leak has come to light, security experts say it effectively torpedoes the security assurances offered by Secure Boot.
“It’s a big problem,” said Martin Smolár, a malware analyst specializing in rootkits who reviewed the Binarly research and spoke to me about it. “It’s basically an unlimited Secure Boot bypass for these devices that use this platform key. So until device manufacturers or OEMs provide firmware updates, anyone can basically… execute any malware or untrusted code during system boot. Of course, privileged access is required, but that’s not a problem in many cases.”
Binarly researchers said their scans of firmware images uncovered 215 devices that use the compromised key, which can be identified by the certificate serial number 55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4. A table appearing at the end of this article lists each one.
The researchers soon discovered that the compromise of the key was just the beginning of a much bigger supply-chain breakdown that raises serious doubts about the integrity of Secure Boot on more than 300 additional device models from virtually all major device manufacturers. As is the case with the platform key compromised in the 2022 GitHub leak, an additional 21 platform keys contain the strings “DO NOT SHIP” or “DO NOT TRUST.”
First “Miss AI” contest sparks ire for pushing unrealistic beauty standards
Wolverine Gets a Rounded Butt Xbox Controller to Compete With Deadpool
Reddit changes have blocked all search engines except Google amid AI ‘misuse’
Windows 11 insider build brings wireless Android phone access to File Explorer