All of my opinions are italicized and sources are in blue.
As reported by BleepingComputer,
The source code for Grand Theft Auto 5 was reportedly leaked on Christmas Eve, a little over a year after the Lapsus$ threat actors hacked Rockstar games and stole corporate data.
Links to download the source code were shared on numerous channels, including Discord, a dark web website, and a Telegram channel that the hackers previously used to leak stolen Rockstar data.
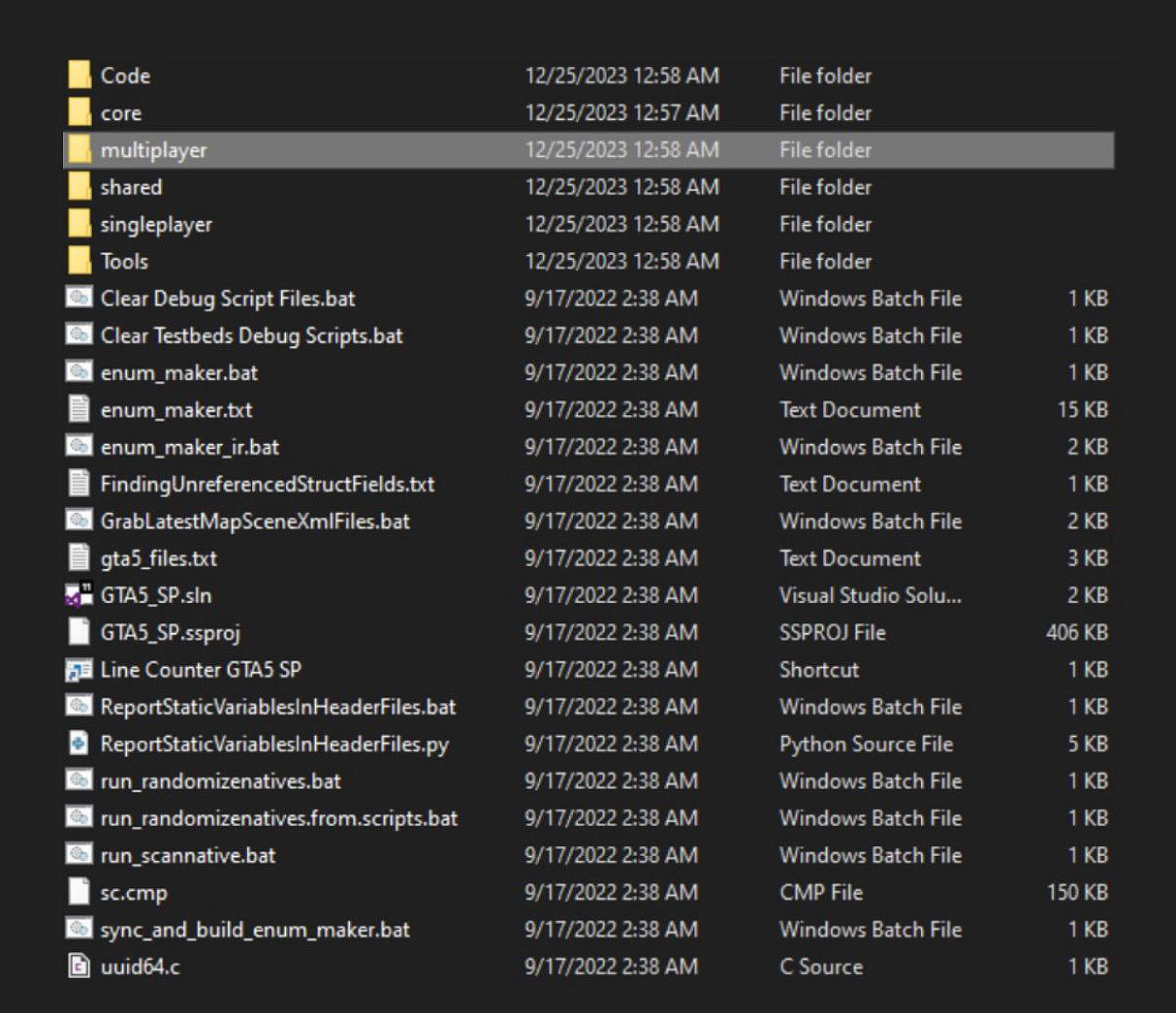
In a post to a Grand Theft Auto leak channel on Telegram, the channel owner known as ‘Phil’ posted links to the stolen source code, sharing a screenshot of one of the folders.
Rockstar Games was hacked in 2022 by members of the notorious Lapsus$ hacking group, who gained access to the company’s internal Slack server and Confluence wiki.
At the time, the threat actors claimed to have stolen the GTA 5 and GTA 6 source code and assets, including a GTA 6 testing build, with some of the stolen content leaked on forums and Telegram. The threat actor also shared GTA 5 source code samples as proof that they had stolen the data.
Security research group vx-underground says they spoke to the leaker on Discord, who said the source code was leaked sooner than expected.
“They claim to have received the source code August, 2023,” reads a post by vx-underground.
“Their motivation was to combat scamming in the GTA V modding scene, many people were allegedly scammed by people claiming to have the GTA V source code.”
As reported by guru3D,
NVIDIA has formally introduced the GeForce RTX 4090D graphics card, specifically engineered for the Chinese market. This release is a response to the October restriction by the United States Federal Trade Commission (US-FTC) prohibiting the export of RTX 4090 and other AI GPUs to China. The RTX 4090D is tailored to comply with the US-FTC’s export limitations, featuring diminished AI inference capabilities in comparison to the global RTX 4090 model. To ensure compliance, NVIDIA has incorporated several technical measures. These include performance constraints at the firmware and driver levels, a unique ASIC code, and a distinct device ID that hinders BIOS modifications from the standard RTX 4090. Additionally, the RTX 4090D utilizes a variant of the 5 nm AD102 GPU with an altered core configuration.
Technically, the AD102 silicon of the original RTX 4090 comprises 72 TPCs (144 SM), enabling 64 TPCs (128 SM). The RTX 4090D, however, employs 57 TPCs (114 SM), leading to a reduction in CUDA cores, Tensor cores, and RT cores. Specifically, the RTX 4090D houses 14,592 CUDA cores, 456 Tensor cores, and 114 RT cores, compared to the 16,384 CUDA cores, 512 Tensor cores, and 128 RT cores in the standard RTX 4090. Both models operate at similar clock speeds, with a maximum boost clock of 2.52 GHz, but the RTX 4090D has a 25 W lower total graphics power (TGP). The memory subsystem in both versions remains consistent.
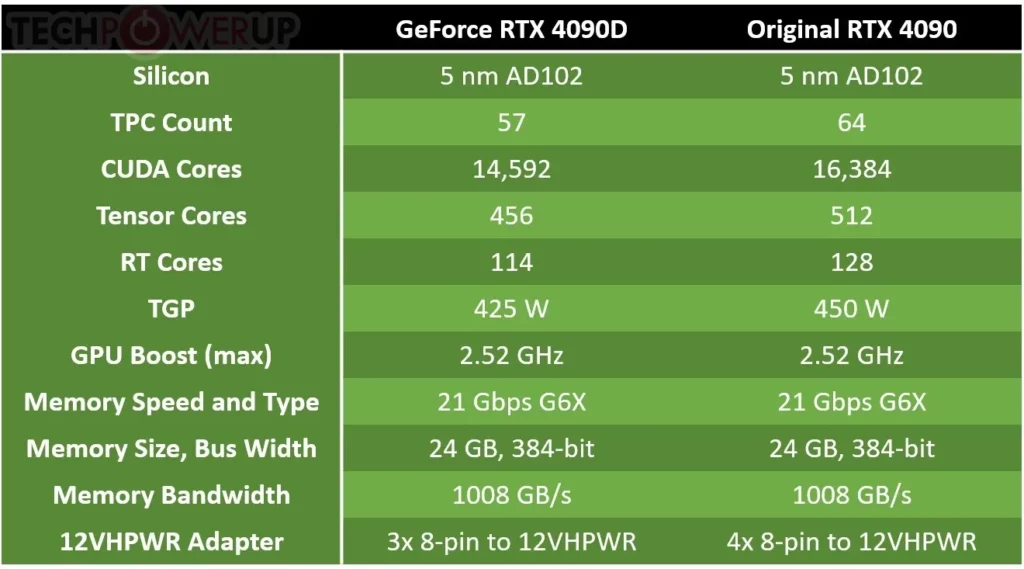
Furthermore, the RTX 4090D’s overclocking potential is limited, with reduced slider limits, to prevent achieving AI inference performance on par with the standard RTX 4090. NVIDIA has priced the RTX 4090D at RMB ¥12,999 ($1,850).
As reported by Gizmodo,
What happens when you hack a cybersecurity researcher? Kaspersky, a Moscow-based security firm, presented new details regarding zero-day vulnerabilities in Apple products on Wednesday. Kaspersky researchers are calling this the most sophisticated attack they’ve ever seen, exposing a previously unknown hardware feature. The attack has been front of mind for Kaspersky researchers because it’s been used against them for the last four years.
“This is no ordinary vulnerability,” said Kaspersky’s Boris Larin in a research paper Wednesday. “What we do know—and what this vulnerability demonstrates—is that advanced hardware-based protections are useless in the face of a sophisticated attacker as long as there are hardware features that can bypass those protections.”
The vulnerability, which researchers call “Operation Triangulation,” was presented at a hacker conference in Germany this week. The complex attack starts with a malicious iMessage attachment, and it doesn’t even need to be clicked to start the process. Then, four distinct zero-day vulnerabilities are used to obtain full control over a device, transmitting microphone recordings, photos, geolocation, and other sensitive data to attacker-controlled servers. This hack was potentially used against thousands of iPhones in Russia, according to Ars Technica, but exposes a hardware vulnerability in Macs, iPods, Ipads, Apple TVs, and Apple Watches.
Hackers were able to bypass hardware-based memory protections that ensure a hacker can’t fully control an Apple device even if it accesses a device’s kernel memory, the core of iOS. This protection has rarely ever been defeated before but is present in Apple’s latest M1 and M2 CPUs. Researchers assume this hardware feature may have been used for debugging or testing purposes by Apple engineers, or that it was included by mistake. Apple has since patched these four vulnerabilities.
This specific hack against a small number of Kaspersky researchers came to light in June, but Russian cybersecurity officials quickly reported that thousands of government officials were also subject to similar attacks. The Russian government accused Apple and the US National Security Agency of colluding on this attack, but Kaspersky researchers, Apple, or the NSA have not confirmed these claims.
Though these bugs are now patched, researchers warn that zero-day vulnerabilities in the hardware of products, such as the one found here, suggest “a flawed approach.” Apple’s hardware systems seem to rely on “security through obscurity,” but as attackers get more advanced, Kaspersky alleges these systems will never truly be secure.
As reported by Ars Technica,
Just before Christmas, Apple pulled two of its latest smartwatches from stores. The cause was not an unwelcome visit from the ghost of mechanical timepieces past but the International Trade Commission, which found that the California-based computer maker had infringed on some patents, resulting in the ITC banning the import of said watches. Yesterday, Reuters reported that Apple filed an emergency request for the courts to lift the ban and will appeal the ITC ruling.
And today, the US Court of Appeals for the Federal Circuit granted Apple’s wish, pausing the ban while it considers the tech company’s argument.
Apple’s watch problems started back in January. That’s when a court found that the light-based pulse oximetry sensor (found on the back of the watches) infringed patents held by Masimo, a medical device manufacturer also based in California.
At the time, Apple said since Masimo was not a consumer-focused company, it chose not to collaborate or acquire the medical device maker. Masimo, for its part, said that Apple led it on in discussions then took its idea and hired away Masimo engineers.
In October, the ITC upheld the ruling of infringement and started the process to ban imports of the watches, giving US President Joe Biden’s administration 60 days to review the case and possibly veto the ruling.
But the Biden administration has chosen not to interfere, unlike in 2013 when the Obama administration vetoed a ban on iPhones and iPads during a patent dispute between Apple and Samsung. Although the ITC’s import ban on Apple Watch Series 9 and Ultra 2 models was supposed to go into effect on December 26, Apple pulled the watches from sale a few days early. The older Apple Watch SE, which doesn’t use the infringing blood oxygen sensor, remains on sale.
“We strongly disagree with the USITC decision and resulting exclusion order, and are taking all measures to return Apple Watch Series 9 and Apple Watch Ultra 2 to customers in the US as soon as possible,” Apple said in a statement.
Apple had asked the CAFC to pause the ban until US Customs and Border Protection decides whether redesigned Apple Watches no longer infringe on Masimo’s patents, a decision that should be reached by January 12. Now the court has given the ITC a deadline of January 10 to respond to Apple.
Using AI and beavers to fight droughts in California
LG makes bipedal robot that can watch your pets, discern your emotions
Steam Deck D-pads with bugs in them
Nintendo reveals most downloaded Switch games in Japan; Tears of the Kingdom loses to $3 fruit matching game, Suika Game