All of my opinions are italicized and sources are in blue.
Introduced by US representatives Warren Davidson and Sara Jacobs, the amendment, first reported by WIRED, would prohibit US military agencies from “purchasing data that would otherwise require a warrant, court order, or subpoena” to obtain. The ban would cover more than half of the US intelligence community, including the NSA, the Defense Intelligence Agency, and the newly formed National Space Intelligence Center, among others.
In a separate but related push last week, members of the House Judiciary Committee voted unanimously to advance legislation that would extend similar restrictions against the purchase of Americans’ data across all sectors of government, including state and local law enforcement. Known as the “Fourth Amendment Is Not For Sale Act,” the bill will soon be reintroduced in the Senate as well by one of its original 2021 authors, Ron Wyden, the senator’s office confirmed.
“Americans of all political stripes know their Constitutional rights shouldn’t disappear in the digital age,” Wyden says, adding that there is a “deep well of support” for enshrining protections against commercial data grabs by the government “into black-letter law.”
The extent to which the NSA in particular uses data brokers to obtain location and web-browsing data is unclear, though the agency has previously acknowledged using data from “commercial” sources in connection with cyber defense. Regardless, the NSA’s lawyers have authored extensive guidelines for acquiring commercially available data, particularly when it belongs to US companies or individuals. Some of the rules prescribed by the agency’s lawyers remain classified.
The malware, dubbed CherryBlos by researchers from security firm Trend Micro, has been embedded into at least four Android apps available outside of Google Play, specifically on sites promoting money-making scams. One of the apps was available for close to a month on Google Play but didn’t contain the malicious CherryBlos payload. The researchers also discovered suspicious apps on Google Play that were created by the same developers, but they also didn’t contain the payload.
The apps took great care to conceal their malicious functionality. They used a paid version of commercial software known as Jiagubao to encrypt code and code strings to prevent analysis that can detect such functionality. They also featured techniques to ensure the app remained active on phones that had installed it. When users opened legitimate apps for Binance and other cryptocurrency services, CherryBlos overlaid windows that mimicked those of the legitimate apps. During withdrawals, CherryBlos replaced the wallet address the victim selected to receive the funds with an address controlled by the attacker.
The most interesting aspect of the malware is its rare, if not novel, feature that allows it to capture mnemonic passphrases used to gain access to an account. When the legitimate apps display passphrases on phone screens, the malware first takes an image of the screen and then uses OCR to translate the image into a text format that can be used to raid the account.
Not only are they offering a full selection of replacement parts for both the standard and Elite Xbox controllers, they’ve also provided written instructions and step-by-step video guides on how to install your new parts.
Of course, these parts were already available from third party sellers, and iFixit naturally has repair guides for all the different flavors of Xbox controllers. Nothing about what Microsoft is doing here makes the Xbox controller fundamentally any easier to repair than it was previously. But the fact that the company isn’t treating their customers like adversaries is a step in the right direction.
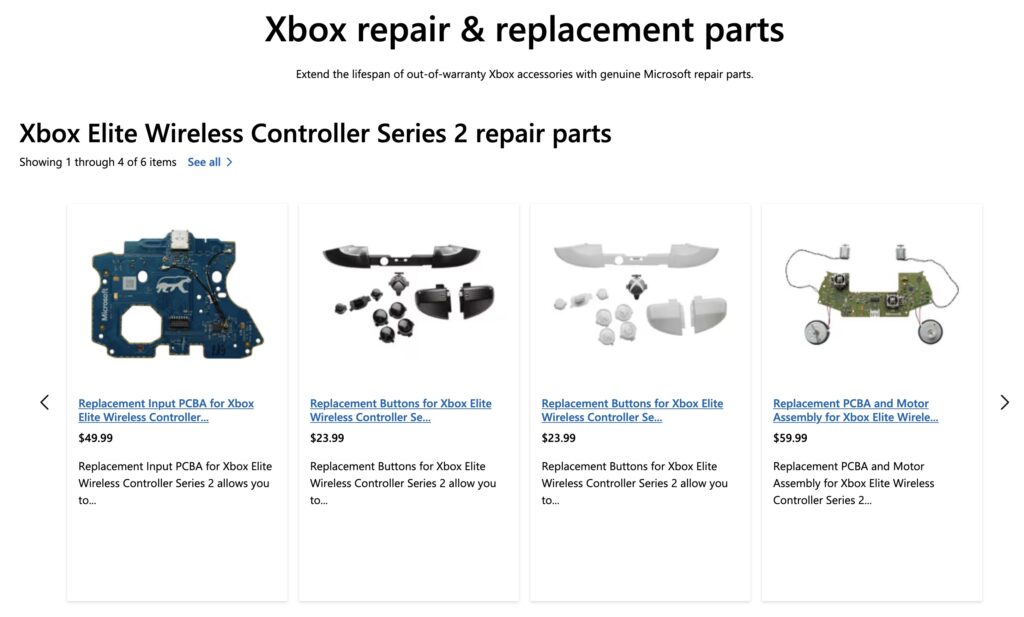
However, the Xbox Series X SSD has been designed in such a way that it makes it impossible to repair a fault yourself if something goes awry. So there is still some work to do before Microsoft products are fully repairable.
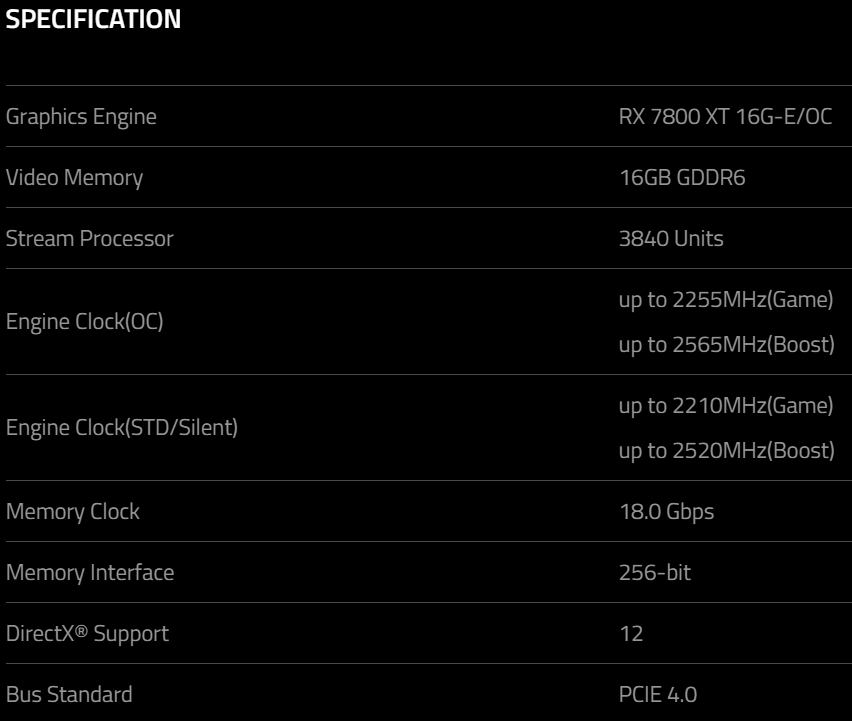
If you’re having a tough day at work, consider that it could always be worse. For example, someone over at AMD licensee PowerColor is in a heap of hurt right now, because the company accidentally posted a full listing for the Radeon RX 7800 XT graphics card, complete with specifications.
There’s been a mid-range hole in AMD’s Radeon 7000 series since it launched last year, with the low-end RX 7600 at $270 being the only other card besides the $900 RX 7900 XT and $1000 RX 7900 XTX. AMD has confirmed that new “enthusiast” cards are coming before the end of October, presumably in between those two price points and at the 7700/7800 level. But PowerColor’s full-page listing, shared on Twitter almost immediately and since taken down, is more or less an official confirmation of its existence.
Assuming that PowerColor’s specifications are accurate, the Radeon RX 7800 XT may feature 16% fewer stream processors than the existing Radeon RX 6800 XT.
Teslas are among the most popular electric cars on the market, which makes them an easy target for hackers. Now, a team of security researchers from TU Berlin has found a way to exploit the MCU found in modern Tesla vehicles to unlock paid features and more. To execute the attack, the researchers exploited a known flaw in AMD’s processor that controls Tesla’s MCU. In Tesla parlance, MCU stands for Media Control Unit, and it controls the touch screen, navigation, and entertainment systems.
According to the researchers, they used a voltage fault injection attack (a certain class of attacks) against the MCU-Z. This class of attacks is also known as ‘voltage glitching,’ and is a known attack vector for Zen 2- and Zen 3-based processors; it also affects the Ryzen SoC used in Tesla’s MCU-Z. Utilizing multiple connections to the power supply, BIOS SPI chip, and SVI2 bus, the researchers performed a voltage fault injection attack on the MCU-Z’s Platform Security Processor. With a successful attack, objects stored in the Trusted Platform Module (TPM) can be decrypted.
Hasbro wants to bring back 360/PS3 Transformers games, but Activision lost them
Elden Ring Player beats game with electric saxophone
NASA loses, then regains contact with Voyager 2
Company creates water soluble circuit boards to replace shredding and burning
Baldur’s Gate 3 launched, rated Mature for a reason